Validating Azure AD B2C Tokens
I recently ran into an issue where I needed to help a customer validate an Azure AD B2C JWT access token. We tend to take JWT tokens for granted and sometimes forget that they should be validated by the application. I thought this was going to be pretty straight-forward to solve since Azure AD B2C is effectively Azure AD under the hood. I was wrong.
I initially thought browsing to the OIDC metadata endpoint would reveal the info I needed to validate the signature of the JWT but finding the endpoint was my first challenge.
This doc came in handy as I needed more details on B2C tokens: https://docs.microsoft.com/azure/active-directory-b2c/tokens-overview
I learned that each Azure AD B2C User Flow has its own metadata endpoint.
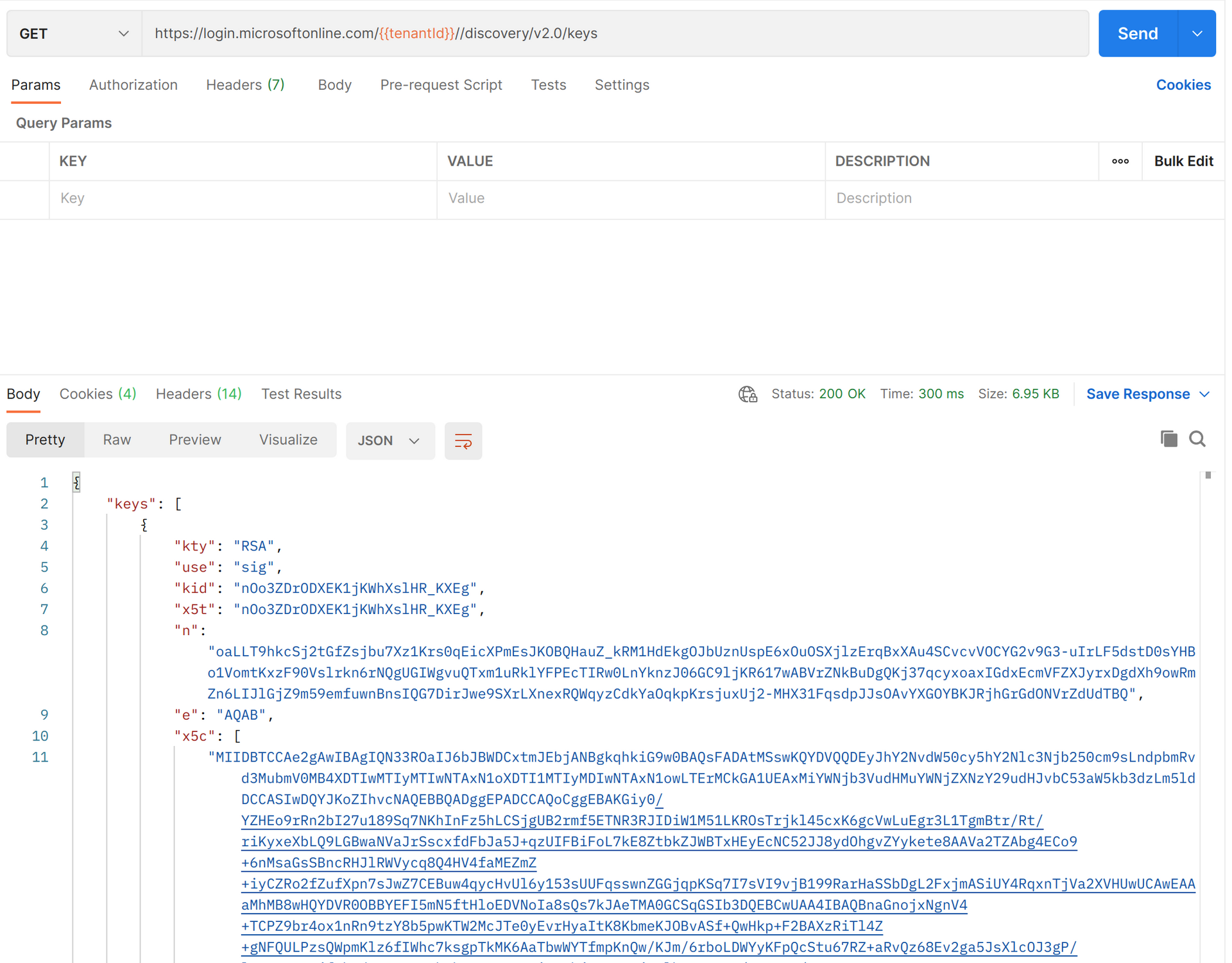
Inside the JSON response, you will see a jwks_uri
If you navigate to this URI, you will see the details on the key that signed the token.
More specifically, you will see the e value which is the exponent and the n value which is the modulus.
When folks want to validate the signature of a token, they’ll typically browse to https://jwt.io and paste in the access token to view the results.
Let’s go try it.
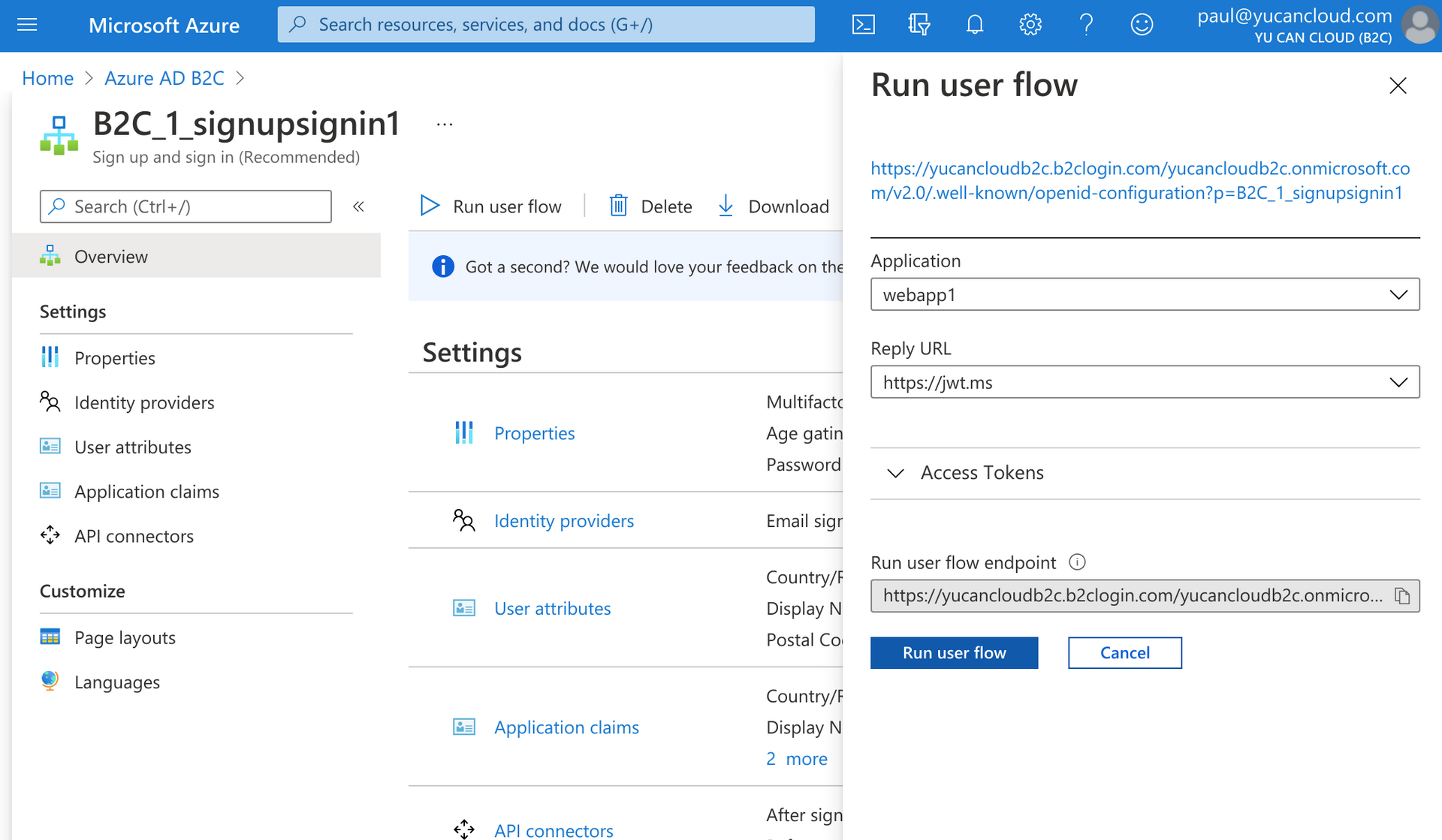
First, we’ll need a JWT so the easiest way to do this is to run a user flow. Here I am testing with my B2C_1_signupsignin1 user flow and against my webapp1 application which has been configured to redirect to https://jwt.ms.
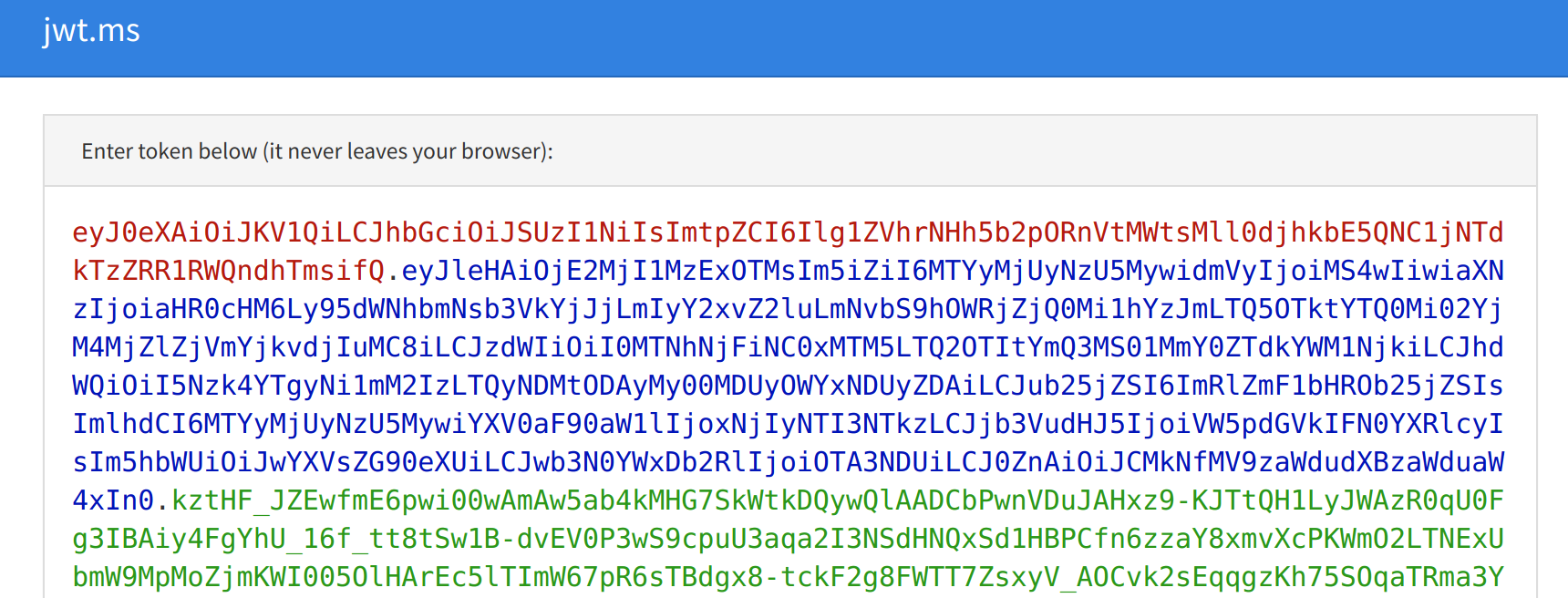
You’ll need to enter your credentials (or signup) and eventually you will land on the jwt.ms website which includes your JWT access token. Copy the value from the textbox.
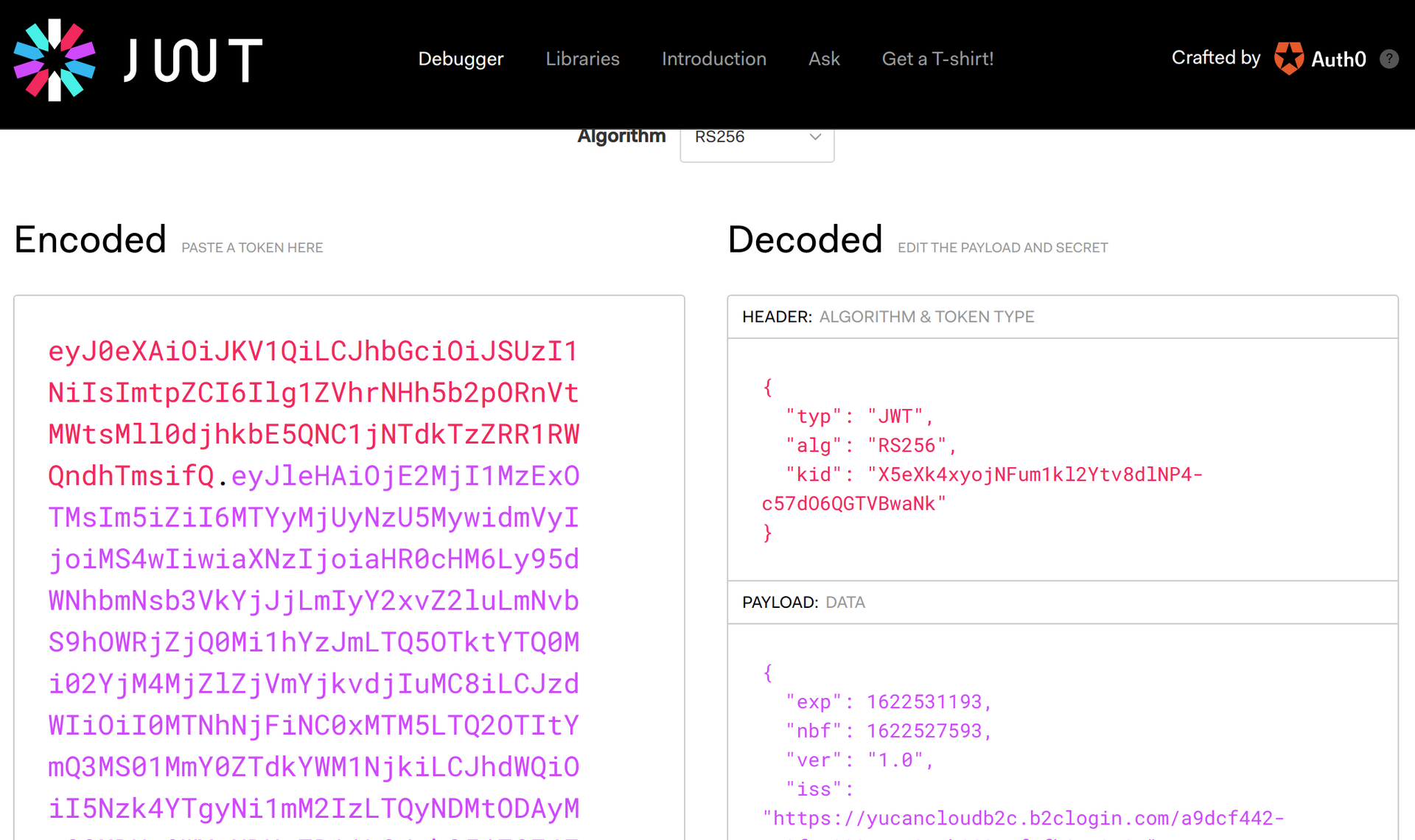
Now, browse to https://jwt.io and paste in your access token into the Encoded text box - where it says Paste a token here.
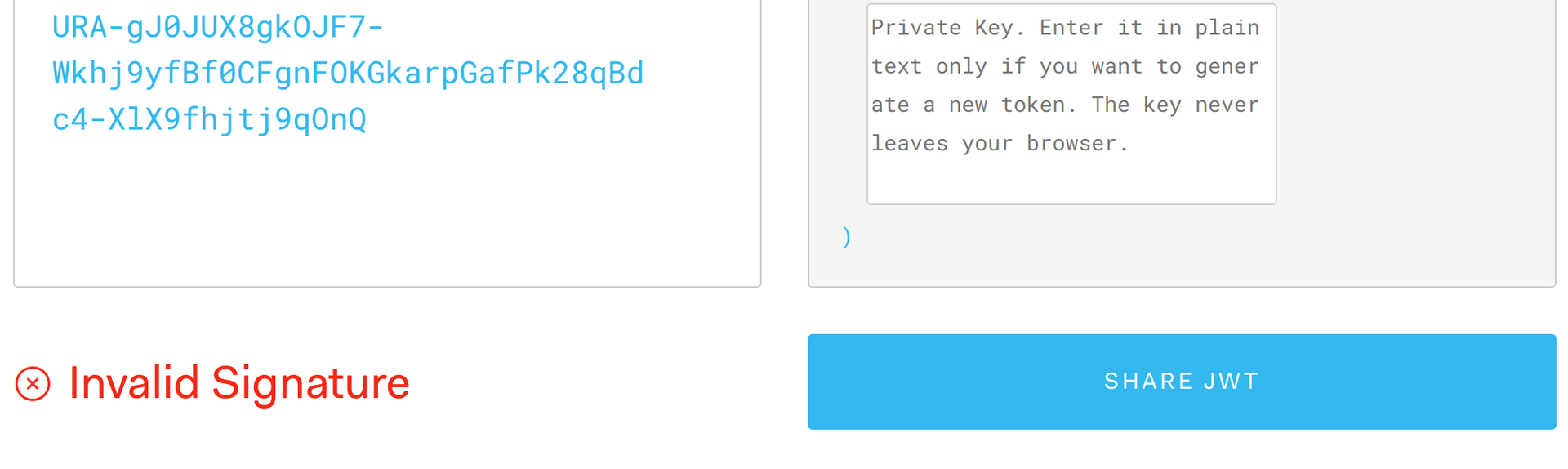
Uh-oh, if you take a look at the bottom of the token text box, you’ll notice it says Invalid Signature.
You might be asking… why does this happen? Does this mean the token is not valid or is is susceptible to being stolen or spoofed? No. The signature cannot be verified by jwt.io since it is not aware of the public key that was used to sign it.
Great! So where’s the public key?!?
Do you remember me sending you to the metadata endpoint for your B2C user flow and following the JSON response to the jwks_uri? If the public key was included in the keys metadata endpoint, jwt.io would have been able to use that to validate the signature. Here is what the keys metadata endpoint looks like for a non-B2C Azure AD tenant.
The
x5celement represents the public key.
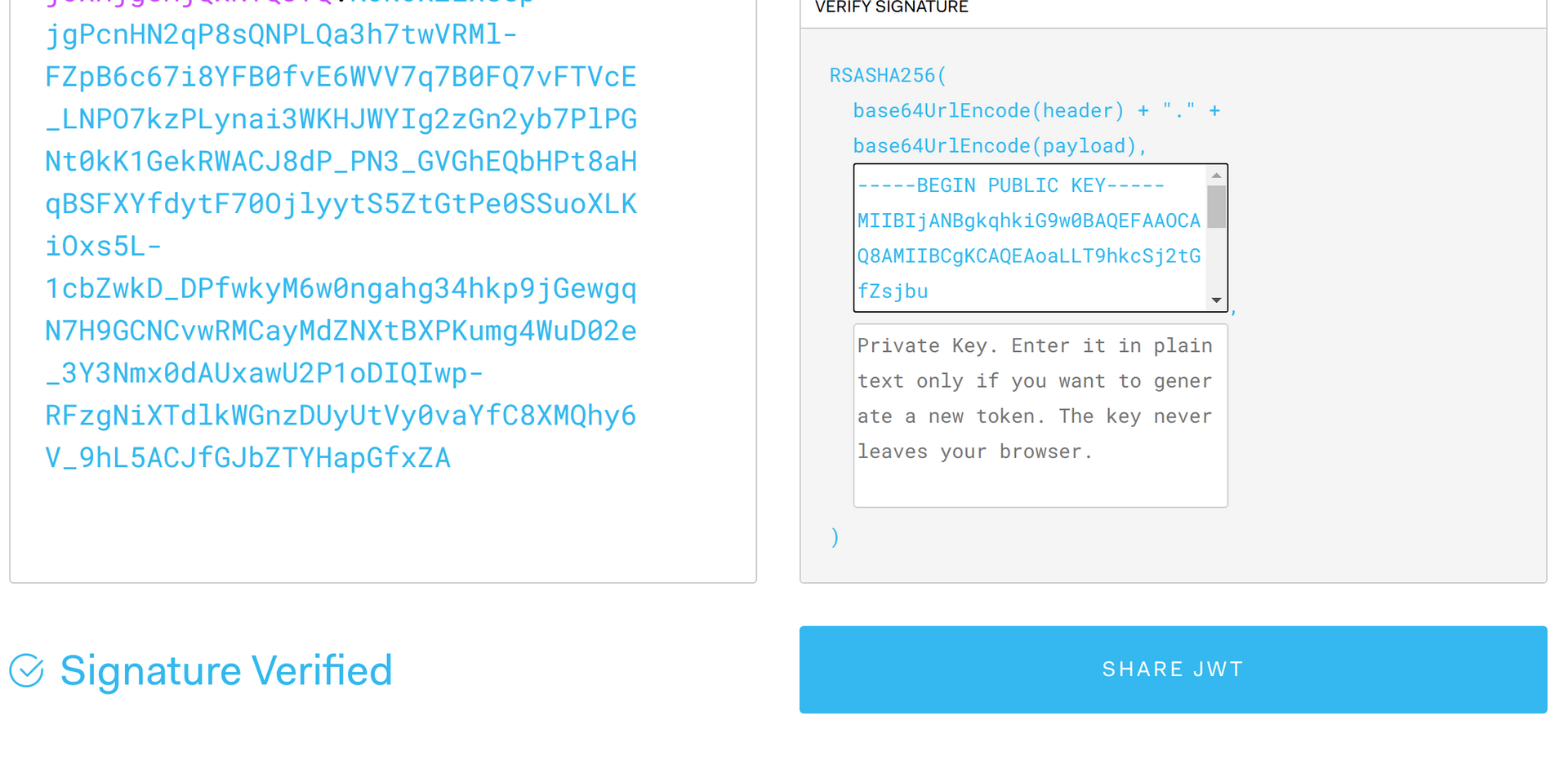
When the public key is accessible, there will be no issues in simply pasting in the token and having it verify the signature.
Since we are dealing with Azure AD B2C, we’ll need to manually generate the public key and manually paste it into the public key text box.
Thankfully, someone has been playing in the Go Playground and made this:
https://play.golang.org/p/7wWMBOp10R
If you paste in your entire key from the discovery keys endpoint for your user flow and run the code, you will have a public key to enter in to jwt.io. Enter the public key into this textbox and the token’s signature will be validated.